
Loading...
Free consultation with ASO specialists
Doing ASO for the first time or have no idea how to carry out targeted optimization of your app?
We offer one-on-one customized services provided by app marketing specialists
Google forces Android developers to verify their real names: a security innovation for the open ecosystem
2025-09-01
In August 2025, Google published in its official blog 《Improve Android Security Levels》announced that it will extend developer authentication requirements from the Google Play Store to all application distribution channels. This policy covers applications distributed through third-party stores or APK files (such as W2A format), marking the most stringent developer identity management mechanism in the Android ecosystem. Google data shows that the policy originated from the security risks of sideloaded applications, which are more than 50 times higher than those of official stores. Malware, financial fraud, and data theft incidents have become major threats to user safety.
Policy Core: Comprehensive Ban on Anonymous Distribution
The new policy builds a verification system of "omnichannel coverage". No matter whether the application is listed on Google Play, developers of applications distributed through non-official channels must complete identity verification, completely ending the long-standing model of "anonymous development-side loading distribution". With this, Google strengthens the security control of the entire Android application chain.
The policy mainly targets three types of security threats: malware propagation, financial fraud tools and data theft programs. According to a 2019 survey by cybersecurity company Sophos, regions such as Indonesia and Brazil have become heavily affected by malware, with a large number of malicious programs disguised as game cheats widely spread through sideloading. The Baldr virus alone has caused nearly a thousand user information leakage incidents. Google's security team analysis shows that more than 90% of these malicious applications come from unverified anonymous developers, which is the key basis for expanding this policy.
This policy is also a continuation of Google's security strategy since 2023. At that time, Google had already required developers on the Play Store to complete identity verification, and this time it expanded the scope to sideloading channels, forming closed-loop management. "Shixin," an Android certification expert, said that this policy mainly targets risk control for unofficial channels, with limited impact on compliant developers and ordinary users, but will significantly increase the cost for malicious developers to break the law.
Verification Mechanism: Hierarchical Management and Technical Implementation
Google's Developer Verification mechanism adopts a hierarchical design. Individual developers need to provide legal name, address, valid email and mobile phone number; enterprise developers also need to submit the official website address and DUNS number (Dun & Bradstreet number), which is a global unique identifier that helps Google verify the authenticity of the organization.
To support the new policy, Google has developed a new Android Developer Console (ADC) platform as an entry point for non-Play Store developers. This platform integrates authentication, application management, and compliance check functions, using encryption technology to protect developer information, ensuring it is only used for verification purposes and not disclosed to users or third parties. Compared with the old Play Console, ADC specifically optimizes the operational process for non-commercial developers, providing multi-language support and step-by-step guidance.
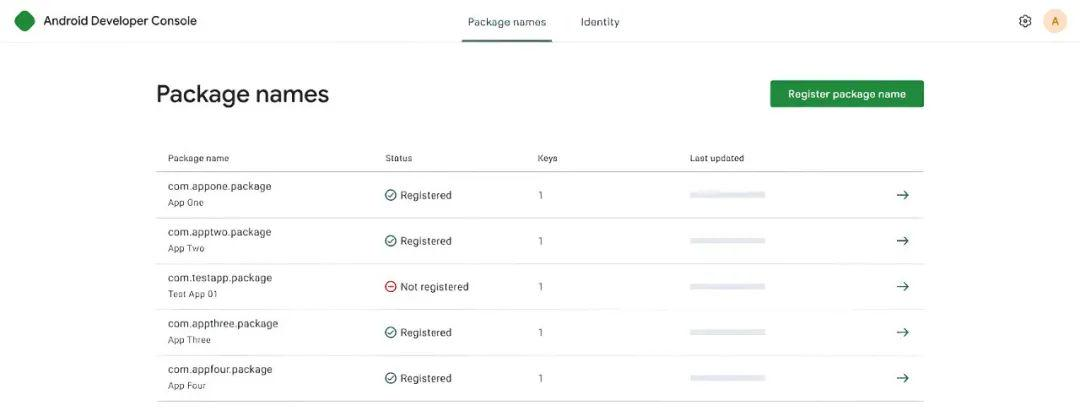
On the distribution type, Google sets two types of options:
-
Commercial distribution: applicable to commercial applications, with a registration fee of 25 USD, no limit on the number of applications and installations, and stricter verification standards;
-
Limited distribution: For non-commercial purposes such as students and open source projects, registration fees are waived, but the number of applications (no more than 5) and the number of installations (cumulative ≤ 1000 times) are limited to prevent abuse.
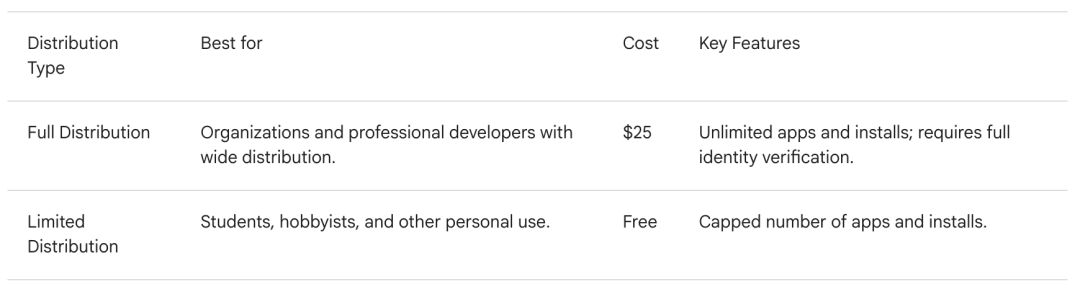
This grading mechanism, while ensuring security, also leaves flexible space for educational institutions and open-source communities. The verification process introduces AI-assisted review, and it is expected that ordinary developers can complete the verification within 3 working days.
Implementation plan: Steady progress in phases
Google announced a clear policy implementation timetable, adopting a gradual strategy of "pilot - promotion - mandatory":
-
August 2025: The policy is officially announced, and the developer consultation channel is opened;
-
October 2025: Initiate invitation-based testing, select developers of different scales to participate in the verification process test;
-
March 2026: The verification system is fully open, and all developers can submit verification applications independently;
-
September 2026: Mandatory pilot launch in Brazil, Indonesia, Singapore, Thailand, where installed apps must be from verified developers;
-
Q1 2027: Complete global enforcement, unverified apps will be blocked by the system.

The selection of pilot regions is based on security risk assessment. Data shows that the malware infection rate of side-loaded apps in Brazil is 3.2 times higher than the global average, and the annual growth rate of financial fraud cases caused by unofficial channel apps in Indonesia reached 47%. These regions are also the fastest-growing markets for Android users, and priority implementation will help control global security risks.
The head of Google's security team said in an interview that the phased implementation is intended to give developers sufficient time to comply, especially small and medium-sized developers and non-commercial development groups. During this period, multiple rounds of training webinars and localized support documents will be provided to help developers in different regions understand the verification requirements.
Industry impact: ecological security and compliance pressure coexist
The new policy will profoundly affect the Android app distribution landscape. Apps that fail verification will be automatically blocked by Google Play Protect. This system performs 125 billion scans daily and has features such as pre-installation checks, real-time behavior analysis, and abuse warning for permissions. Even if side-loading is successful, non-compliant apps will be marked as "potentially harmful apps" and their operation will be restricted.
This policy echoes China's App filing system, indicating that the major global mobile application markets are all evolving toward "developer real-name authentication + distribution compliance." The difference is that Google adopts a combination of enterprise self-certification and technical verification rather than government approval. Hong Yanqing, a professor at Beijing Institute of Technology, pointed out that while this platform-led model improves security, it also needs to be vigilant against the risk of "abuse of review rights."
Compliance challenges vary for different types of developers:
-
Large enterprises: need to update the organizational information management process to ensure the validity of identifiers such as DUNS numbers;
-
Independent developers: need to prepare internationally recognized notarized personal identity documents;
-
Education and open source community: limited distribution can be selected, but the number of applications and scope of dissemination need to be controlled;
-
Developers going overseas: Must meet the requirements of domestic filing and Google verification at the same time. It is recommended to establish a library of compliance documents.
Developers who rely on APK distribution for overseas expansion must complete the preparation of materials before March 2026. Google particularly reminds enterprise developers to ensure that the official website domain name matches the registered name and complete the association verification through Search Console, a process that usually takes 1-2 weeks.
Looking forward: How to balance security and openness
The new policy has triggered a discussion about whether "security enhancement sacrifices the spirit of open source". Google clearly stated in the announcement that the verification policy is only for developer identity and does not limit code open source, and AOSP (Android Open Source Project) still accepts third-party code submission.
After the implementation of the policy, three types of changes may occur in the industry: reshuffle of side-loading market and elimination of non-compliant developers; accelerated integration of regular third-party stores; and more standardized enterprise side-loading mechanism.
From a global regulatory perspective, Google's policies contrast with the EU's Digital Markets Act. The EU is forcing Apple to open sideloading to promote competition, while Google is strengthening control in the open Android ecosystem, reflecting the complex balance of platform regulation between preventing monopolies and avoiding excessive openness.
For users, the new policy will improve the security experience, but experts still suggest keeping alert to abnormal permission requests.
Developer's Guide
Facing the countdown of compliance, developers can take the following measures:
-
Prepare materials in advance: Individual developers need to prepare proof of identity and address; enterprise developers need to apply for a DUNS number (free channel provided by Dun & Bradstreet official website), and unify the official website domain name and registered name;
-
Evaluate distribution channels: non-commercial applications can choose limited distribution to reduce costs;
-
Technical adaptation: test the compatibility of applications in the verification process, especially high-privilege tool class applications;
-
Arrange time reasonably: Complete the verification before the first quarter of 2026 to avoid the peak of audit;
-
Set up compliance positions: Large teams are recommended to have dedicated personnel to track policy dynamics.
Google provides fee reductions and localization guidance for developers in emerging markets, and the ADC platform also has a built-in "compliance self-check tool" to help developers identify material problems in advance.
The Android ecosystem is undergoing a strategic shift from "freedom first" to "security first." Developers may face increased compliance costs in the short term, but will benefit from a healthier market environment in the long run; users will enjoy a safer application experience. As the global mandatory implementation approaches in 2027, this ecological transformation affecting billions of users has entered its countdown.
Facing the upcoming compliance deadline and market changes, ensuring the discoverability and competitiveness of your app is more important than ever. In addition to complying with official requirements, professional App Store Optimization (ASO) can effectively help your app improve on a compliant basis Keyword Rankings With natural traffic. Contact us now to get a customized metadata diagnostic solution and exclusive keyword library suggestions for free, so as to protect your application from going overseas.
Related recommendations

